
Security: Authentication
Indentifying the user to the system.
Most common method: passwords
In Unix, see crypt(3) for more information about the encryption used. See /etc/passwd or /etc/shadow for password files.
Security is compromised if passwords are compromised. There are many ways that this can happen:
Security: Threats
Real story: malicious trap door program left running as "pine".
Real story: UNIX Cloak v1.0
Discussion topic: Open Source vs. Proprietary systems for security?
Recent news item: Trojan Found in libpcap and tcpdump
For privacy or security, some information may need to be encrypted.
We have seen that Unix stores password entries in an encrypted form.
We'll talk a bit more about networks soon, but one of the problems with communicating across many of today's networks is that the information on the network can be seen not only by its intended recipient, but also by many other computers. Encryption has been used for this purpose for centuries, often with the messages being military orders.
Even when a network is not involved, someone may want to encrypt files for privacy.
Original data is called clear text, encrypted version is called cipher text.
Conventional Encryption

The cipher text is a function of the clear text, the encryption algorithm, and the secret key. The algorithm is public! Or at least a good scheme should not rely on the secrecy of the algorithm. It's just the key that is kept secret.
The clear text is a function of the cipher text, the decryption algorithm, and the same secret key. Again, the algorithm is public. The decryption returns the original clear text.
For the encryption to be strong enough, it must be very difficult to figure out the secret key, even given a bunch of cipher texts and the algorithm. Two approaches that an adversary may use are cryptanalysis, where properties of the clear text and the nature of the algorithm are examined to deduce the secret key, and a brute-force attack, where every possible key is tried until one works. For an n-bit key, this means up to 2n keys must be tried, making brute-force attacks expensive. But modern hardware can break a 56-bit key in just a few hours.
Examples:
Problem: how do we tell the intended recipient of our messages what our secret key is, without telling all the world what our secret key is. Perhaps this can be sent securely by some other means, but perhaps the only communication channel is the one we do not trust that led us to employ encryption in the first place.
Public-Key Encryption

Instead of a single key, we have a public key and a private key. The public key is, well, public - anyone who wants to have it, can have it. But the private key is never shared. This idea was proposed in 1976 by Diffie and Hellman.
To transmit a message securely from Alice to Dilbert:
But what if Catbert intercepts the message?
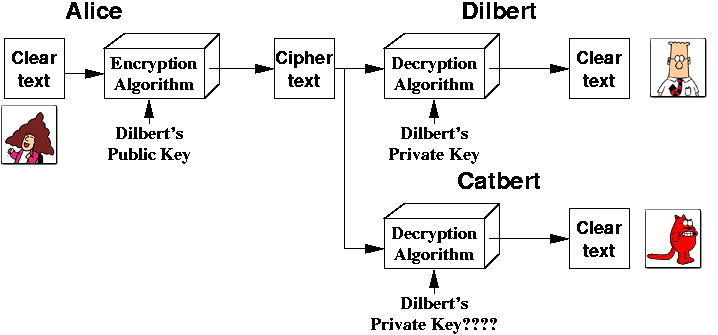
Everything is just fine - even though Catbert, the evil directory of Human Resources, has the cipher text and he can have Dilbert's public key, he does not have Dilbert's private key. So he has no way to intercept the message.
The most popular public-key algorithm is the Rivest-Shamir-Adleman (RSA) Algorithm. It uses the fact that it is relatively easy to compute numbers that are products of large primes, but very difficult to factor the number into those primes.
Secure shell works this way - when you set up ssh, your computer computes its public key and private key. When another computer wants to communicate securely with yours, they exchange public keys and they're off.
There's still a potential problem with the distribution of public keys. Suppose Alice decides to send Dilbert a message for the first time, so she needs his public key. When she makes that request, maybe Dilbert is out of the office, but Catbert pretends to be Dilbert (spoofs his address) and sends his own public key instead. Since Alice didn't know it came from Catbert instead of Dilbert, she gladly encrypts messages intended for Dilbert using the bad public key, and Catbert sits in his office decrypting, soon to fire Alice for what she said about him..
There is a lot more to discuss about encryption, but most of it does not really fit into this course. Some links to visit for more information: